
A lawmaker has called on the Federal Trade Commission (FTC) to investigate Flock for allegedly violating federal law by not enforcing multi-factor authentication (MFA), according to a letter shared with 404 Media. The demand comes as a security researcher found Flock accounts for sale on a Russian cybercrime forum, and 404 Media found multiple instances of Flock-related credentials for government users in infostealer infections, potentially providing hackers or other third parties with access to at least parts of Flock’s surveillance network.
“Flock’s failure to natively support and require phishing-resistant MFA means that if hackers or foreign spies steal, phish, or otherwise learn a law enforcement officer’s Flock password, they can gain access to law-enforcement-only areas of Flock’s website and search the billions of photos of Americans’ license plates collected by taxpayer-funded cameras across the country,” Senator Ron Wyden wrote in the letter addressed to Andrew N. Ferguson, the chairman of the FTC.
💡Do you know anything else about Flock? I would love to hear from you. Using a non-work device, you can message me securely on Signal at joseph.404 or send me an email at joseph@404media.co.
Flock’s automatic license plate reader (ALPR) cameras continuously scan vehicles that pass them, and record their make, model, color, and license plate. The cameras are present in thousands of communities around the U.S., and law enforcement users can search for a specific vehicle to show where it has driven, not just in their own state but potentially across the entire country as part of Flock’s national network. 404 Media previously revealed local police performed Flock lookups on behalf of ICE; that a Texas police officer searched cameras nationwide for a woman who self-administered an abortion; and that ICE and other federal agencies also had direct access to Flock’s national lookup system at one point.
404 Media used a tool called Infostealers.info to search for infostealer infections related to Flock Safety. Infostealers are a type of malware, often hidden in pirated software, that surreptitiously steal essentially all of a victim’s credentials stored in their web browser. Infostealers.info allows essentially anyone to search what it says is data from more than 50 million devices (the company behind the site, Farnsworth Intelligence, markets its infostealer products specifically to debt collectors and couples in divorce proceedings).
That search revealed 85 sets of exposed credentials, including some from government, police department, and Sheriff Office email addresses in Atlanta, Missouri, Michigan, Ohio, Oklahoma, and Texas. It is not clear if the credentials are current, but some of the credentials were harvested by hackers as recently as October, according to the data.
A screenshot of the search results. Redacted by 404 Media.
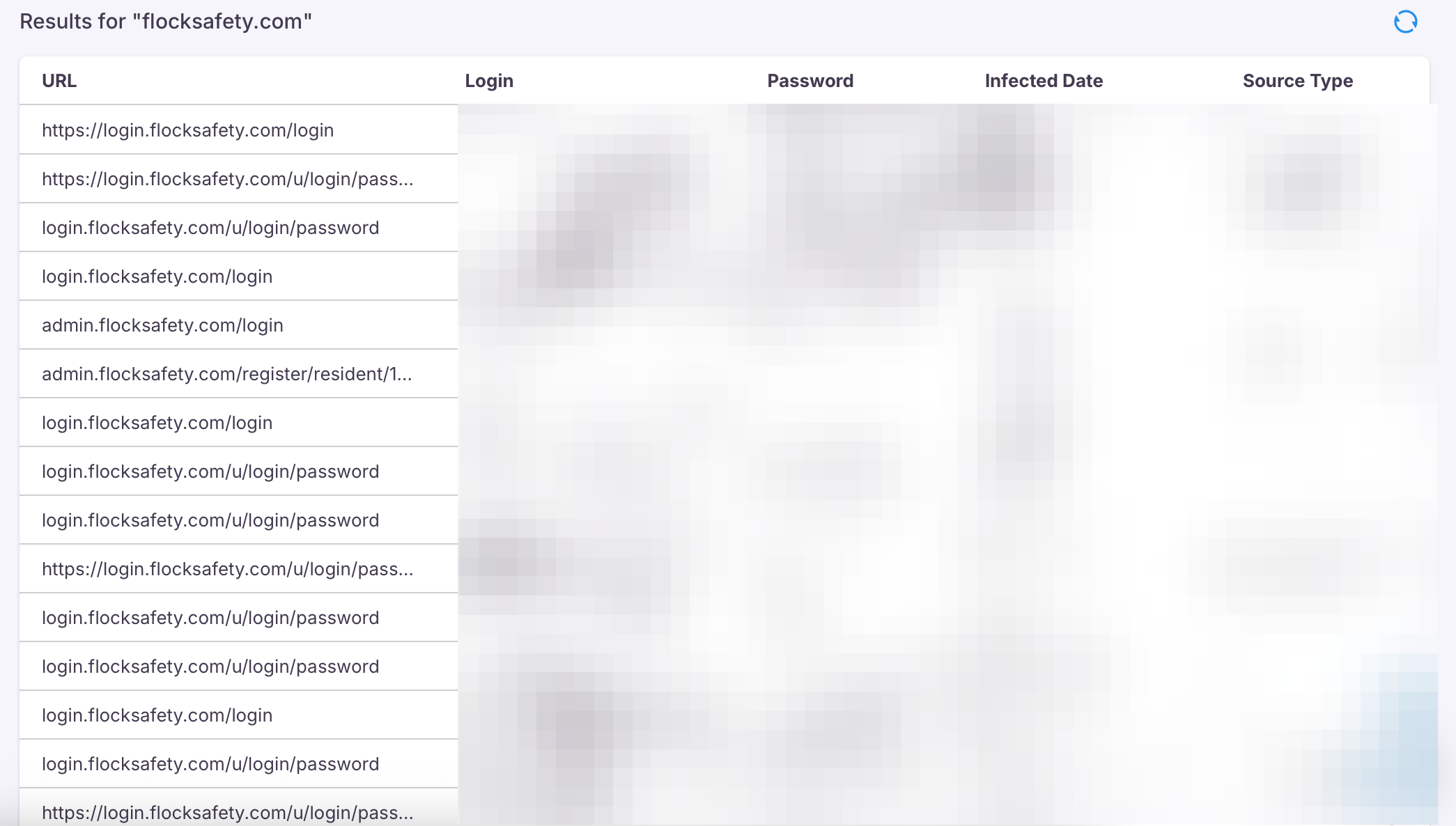
404 Media also used a free tool from cybersecurity company Hudson Rock to search for infostealer infections related to Flock Safety. That search revealed dozens of hacked login credentials for Flock Safety related domains and subdomains, although likely not all are related to law enforcement customers.
The letter says that security researcher Benn Jordan recently provided Wyden’s office “with a screenshot from a Russian-language cybercrime forum in which Flock accounts appear to be offered for sale.”
Armed with exposed credentials, a hacker might be able to log in as the user if the target account does not have MFA-enabled. Senator Wyden’s letter says “While Flock offers support for MFA, a widely recognized cybersecurity best practice, Flock does not require it, which the company confirmed to Congress in October.”
“Moreover, Flock continues to support insecure methods of MFA, such as sending a numeric code to a phone by text message, which is vulnerable to interception and phishing. Flock does not natively support phishing-resistant MFA, which the Cybersecurity and Infrastructure Security Agency calls ‘the gold standard method of [MFA].’ Phishing-resistant MFA is required of federal agencies and mandated by both the Federal Communications Commission and the FTC,” the letter continues.
Wyden says Flock’s lack of MFA enforcement is “likely an unfair business practice prohibited by Section 5 of the FTC Act.” The letter points to other cases in which the FTC has said not requiring MFA does constitute such a practice, and says that the lack of enforcement may also violate state law about data protection and data related to ALPR systems.
“Flock has received vast sums of taxpayer money to build a national surveillance network. But Flock’s cavalier attitude towards cybersecurity needlessly exposes Americans to the threat of hackers and foreign spies tapping this data. Accordingly, we urge the FTC to hold Flock accountable for its negligent cybersecurity practices,” the letter concludes.
Flock did not respond to a request for comment.
From 404 Media via this RSS feed


